Microsoft Azure Authentication¶
In order to support 2-factor authentication, we decided to implement authorization with Microsoft Azure AD. Microsoft has great account management and security. By default, the Microsoft authorization will be enabled to support work/school accounts from all Azure Active Directory tenants. Personal Microsoft accounts are not supported by the default configuration.
Signing in with the a Microsoft account using the default windows login screen¶
To login with a Microsoft account, use the "Sign in" button with the Microsoft logo:
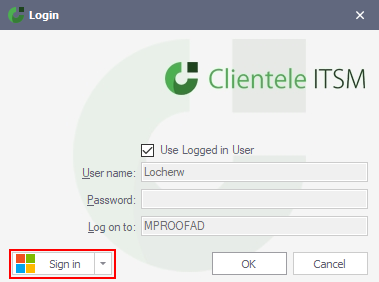
If you have logged in before, a silent login will be attempted with the previous account which was used to login with. If you want to login with another account, press the arrow and select "Other Microsoft Account".

How to Configure a Microsoft account in Clientele¶
To sign in with a Microsoft account, you need to enable the Microsoft Azure AD Cloud Authorization flag for on an active user.
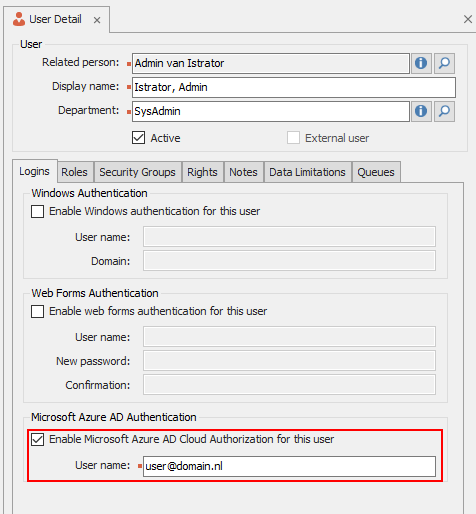
The User name in the Microsoft AzureAD Cloud Authorization section must be entered with the upn (User Principal Name) of the related Microsoft user. This is used to match the user from Microsoft with the Clientele ITSM application user. After this is done, the user will be able to access the application.
Sign in for the first time¶
When you sign in for the first time, you must be a global tenant administrator which can approve the application for all users. This will create a Clientele ITSM "Enterprise application" in the Microsoft Azure Active Directory tenant. If a regular user is signing in the tenant for the first time, a screen may popup asking to ask an administrator for permission:
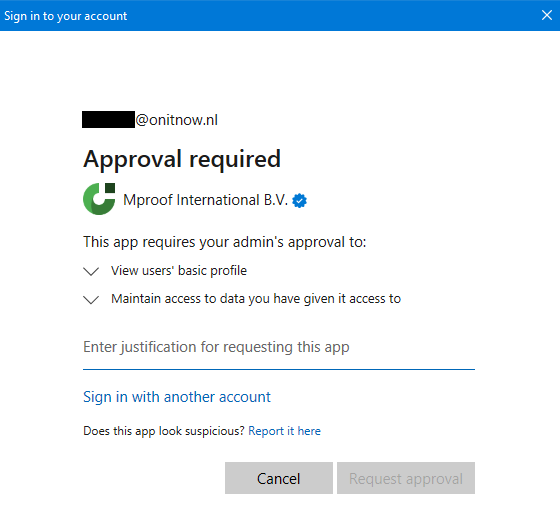
After entering a justification and sending a request approval, the administrator can go to the Azure AD Portal ( https://aad.portal.azure.com/#view/Microsoft_AAD_IAM/ StartboardApplicationsMenuBlade/~/AccessRequests/menuId~/null ) and approve the application to be used by regular users:
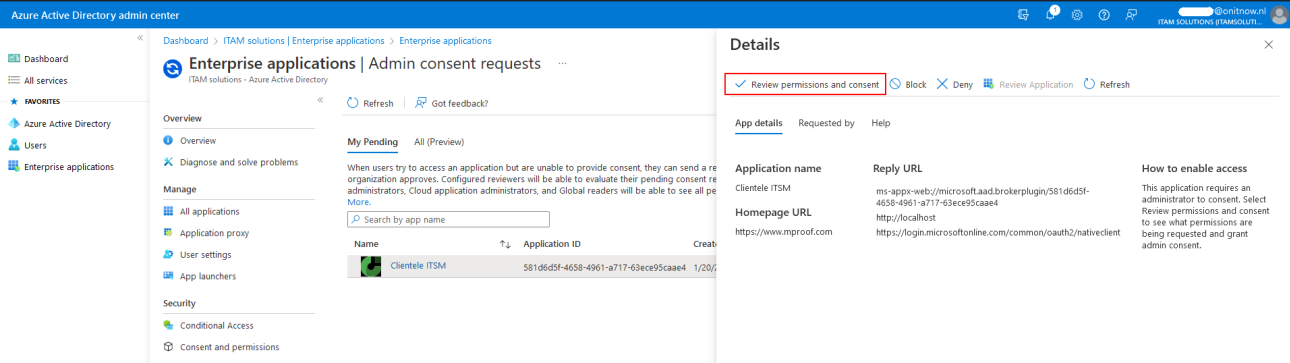
This step however, can be skipped by signing in to Clientele with a global tenant administrator:
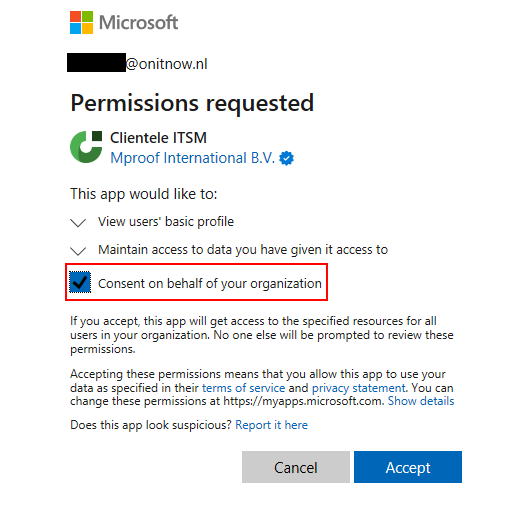
Make sure you check the checkbox "Consent on behalf of your organization", so that all regular users can sign in.
Clientele Client Startup switches for the Microsoft Authorization¶
The Clientele.Loader has several startup switches to configure the authorization process:
/UseLastAzureADCredentials¶
Uses the last Microsoft Azure Active Directory credentials the user used to sign in with, not prompting for re-authentication if possible. After a successful log in, the tokens are stored as an encrypted file in the user's profile. This information is used to sign in the user silently when this startup flag is used, or when the user presses the Microsoft sign in button on the login screen.
/AuthenticationProvider ""¶
The name of the default login provider to use. Supported providers are: Windows, AzureAD and ServiceHub. The default is Windows in an on premise environment, and ServiceHub for a SaaS environment.
/AzureLoginType ""¶
The type of user interface to use when logging in using Microsoft Azure. Supported types are:
- EmbeddedBrowser (or Embedded),
- SystemBrowser (or Browser),
- OperatingSystemBroker (or Broker).
The Embedded Browser is used by default. The OperatingSystemBroker is in preview. The reason to switch the UI type is to be able to troubleshoot or workaround any authorization issues. The Operating System Broker uses a user interface that is build-in to Windows 10 and newer instead of using a browser.
Refreshing the client session¶
During the Microsoft signin proces, an access token is returned. This access token is then send with every request to the web services for authorization. The token is valid for 60 to 90 minutes. When the token becomes invalid, the Clientele ITSM client tries to request a new token silently using the MSAL library.
If this fails, for example because the user changed his/her password or if the user uses the "sign out everywhere" functionality on https://myaccount.microsoft.com/, the system will show the Microsoft login screen and re-asks for the password.
Advanced configuration on the server¶
The sign in of the Microsoft authorization works against in conjunction an application that is registered a Azure AD tenant. The details which application to use are registered in the deployment\web.config file.
The file is located by default in C:\Program files (x86)\Mproof\Clientele ITSM
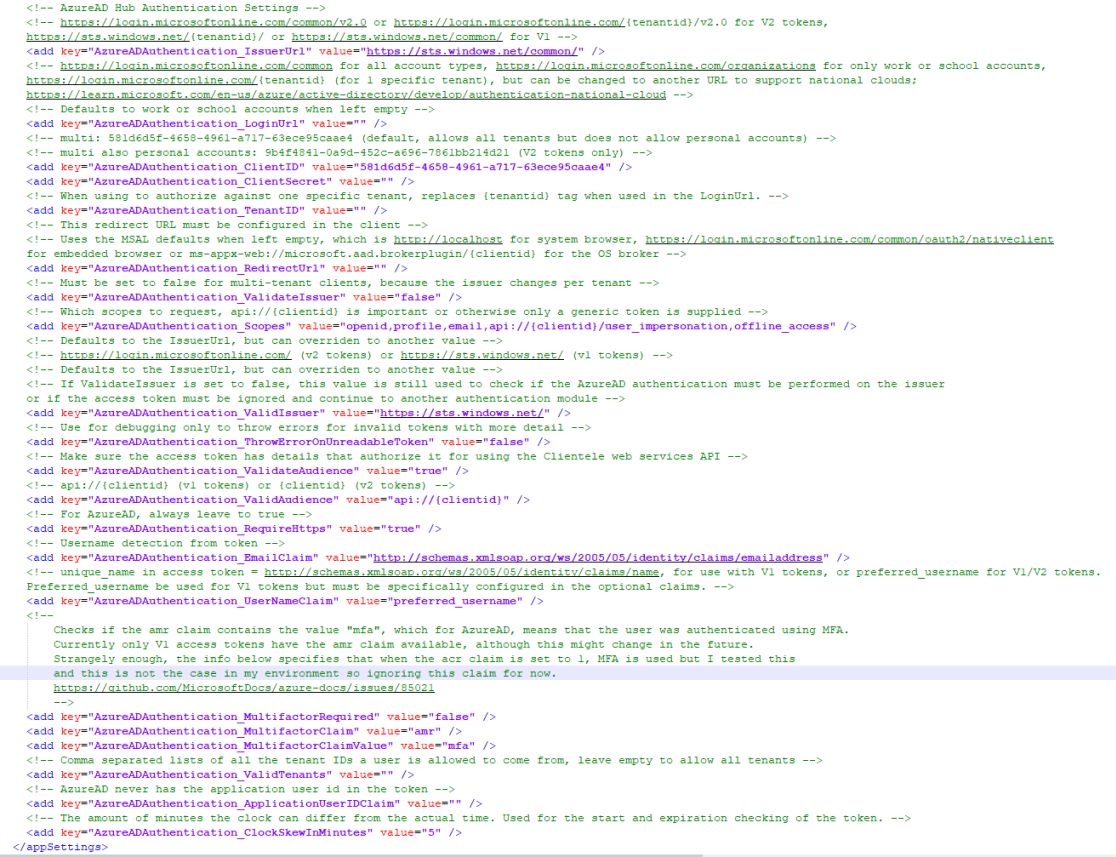
A few settings are interesting for all administrators, others are very advanced and outside the scope of this document.
AzureADAuthentication_MultifactorRequired
Set this to true to only allow sign in of accounts that have logged in with multi factor authentication.
AzureADAuthentication_ValidTenants
This is a comma separated list of tenants that are allowed to sign in. Set the id('s) of your AzureAD tenant(s) in this setting, for example: "2946a7d3-d382-4ebd-af9b-5e3671251aea,28b69537-6b2e-4392-bfa7-4a01ab456f47". By default this is empty to allow users from all tenants to sign in (if they are configured as a user in Clientele ITSM).
If you want to disable the Microsoft authorization, then remove or comment the highlighted line in the deployment\web.config configuration:

If the AzureADAuthentication line is commented using "< !--" and "-->", the Microsoft sign in button will no longer be visible on the client login form.